- Create a web application on port 5 (not only on 5 you can chooose other ports too)
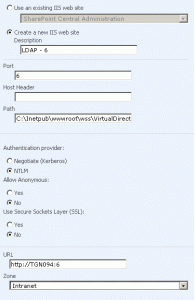
- Extend the web application on to port 6 (which was created on port 5)
copy & paste the below tags exactly after machinkey tag (<machineKey validationKey=”7B896F9AC751CE89F7EEB83E766CF6004D42A26DB9C26C95″ decryptionKey=”2DB30482C44B8B6EE13444509E5243E761241B67209B6FF2″ validation=”SHA1″ />)
<membership defaultProvider=”LDAPMember”>
<providers>
<add name=”LDAPMember” type=”Microsoft.Office.Server.Security.LDAPMembershipProvider, Microsoft.Office.Server, Version=12.0.0.0, Culture=neutral, PublicKeyToken=71E9BCE111E9429C” server=”fivenumber” port=”389″ useSSL=”false” userDNAttribute=”uid” userNameAttribute=”uid” userContainer=”*” userObjectClass=”person” userFilter=”(ObjectClass=person)” scope=”Subtree” otherRequiredUserAttributes=”sn,givenname,cn” />
</providers>
</membership>
<roleManager defaultProvider=”AspNetWindowsTokenRoleProvider” enabled=”true” cacheRolesInCookie=”true” cookieName=”.PeopleDCRole”>
<providers>
<add name=”LDAPRole” type=”Microsoft.Office.Server.Security.LDAPRoleProvider, Microsoft.Office.Server, Version=12.0.0.0, Culture=neutral, PublicKeyToken=71E9BCE111E9429C” server=”fivenumber” port=”389″ useSSL=”false” groupContainer=”*” groupNameAttribute=”cn” groupMemberAttribute=”member” userNameAttribute=”uid” dnAttribute=”fullname” groupFilter=”(ObjectClass=dominogroup)” scope=”Subtree” />
</providers>
</roleManager>
Register the Membership Provider in Web.config file of web application (created on port 5)
copy & paste the below tags exactly after machinkey tag (<machineKey validationKey=”17546320333E569C03469848807DDC42B88B99B6467F6172″ decryptionKey=”B8E349D60494DDF780898F55B74024D00048D5EF4F956BCB” validation=”SHA1″ />)
<membership defaultProvider=”LDAPMember”>
<providers>
<add name=”LDAPMember” type=”Microsoft.Office.Server.Security.LDAPMembershipProvider, Microsoft.Office.Server, Version=12.0.0.0, Culture=neutral, PublicKeyToken=71E9BCE111E9429C” server=”fivenumber” port=”389″ useSSL=”false” userDNAttribute=”uid” userNameAttribute=”uid” userContainer=”*” userObjectClass=”person” userFilter=”(ObjectClass=person)” scope=”Subtree” otherRequiredUserAttributes=”sn,givenname,cn” />
</providers>
</membership>
<roleManager defaultProvider=”LDAPRole” enabled=”true” cacheRolesInCookie=”true” cookieName=”.PeopleDCRole”>
<providers>
<add name=”LDAPRole” type=”Microsoft.Office.Server.Security.LDAPRoleProvider, Microsoft.Office.Server, Version=12.0.0.0, Culture=neutral, PublicKeyToken=71E9BCE111E9429C” server=”fivenumber” port=”389″ useSSL=”false” groupContainer=”*” groupNameAttribute=”cn” groupMemberAttribute=”member” userNameAttribute=”uid” dnAttribute=”fullname” groupFilter=”(ObjectClass=dominogroup)” scope=”Subtree” />
</providers>
</roleManager>
Register the Membership Provider in Web.config file of extended web application (which was extended on port 6)
copy & paste the below tags exactly after machinkey tag (<machineKey validationKey=”17546320333E569C03469848807DDC42B88B99B6467F6172″ decryptionKey=”B8E349D60494DDF780898F55B74024D00048D5EF4F956BCB” validation=”SHA1″ />)
<membership defaultProvider=”LDAPMember”>
<providers>
<add name=”LDAPMember” type=”Microsoft.Office.Server.Security.LDAPMembershipProvider, Microsoft.Office.Server, Version=12.0.0.0, Culture=neutral, PublicKeyToken=71E9BCE111E9429C” server=”fivenumber” port=”389″ useSSL=”false” userDNAttribute=”uid” userNameAttribute=”uid” userContainer=”*” userObjectClass=”person” userFilter=”(ObjectClass=person)” scope=”Subtree” otherRequiredUserAttributes=”sn,givenname,cn” />
</providers>
</membership>
<roleManager defaultProvider=”LDAPRole” enabled=”true” cacheRolesInCookie=”true” cookieName=”.PeopleDCRole”>
<providers>
<add name=”LDAPRole” type=”Microsoft.Office.Server.Security.LDAPRoleProvider, Microsoft.Office.Server, Version=12.0.0.0, Culture=neutral, PublicKeyToken=71E9BCE111E9429C” server=”fivenumber” port=”389″ useSSL=”false” groupContainer=”*” groupNameAttribute=”cn” groupMemberAttribute=”member” userNameAttribute=”uid” dnAttribute=”fullname” groupFilter=”(ObjectClass=dominogroup)” scope=”Subtree” />
</providers>
</roleManager>
After completing the above steps go to
Central Administration > Application Management > Authentication Providers
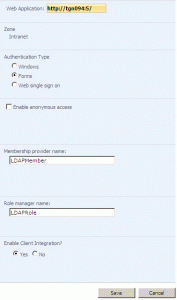
Click on the extended web application (2nd one in the row)
- Select the Authentication Type to ‘Forms’
- Enter the Membership Provider Name as ‘LDAPMember’
- Enter the Role Manager Name as ‘LDAPRole’
Click ‘Save‘
After completing the above configuration settings
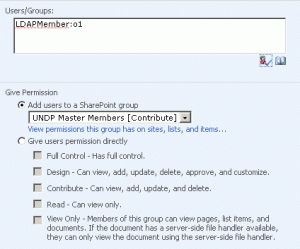
Add the LDAP user in port 5 site.
Now, try to access the extended web application which was created on port 14 with LDAP username and password

Hi
in share point 2010 ldaprole:groupname is not working.
selcuk yazar.